Cyber security firm saw attacks rise by 20% during 2020
Trend Micro found attackers also heavily targeted VPNs


According to a new Trend Micro report, pandemic-related threats contributed to a marked rise in cyber security threats in 2020. The company saw 62.6 billion cyber security threats in 2020, a 20% increase.
The Trend Micro 2020 Annual Cybersecurity Report noted a slew of pandemic-related attacks as online criminals seek to exploit the crisis. Trend Micro detected nearly 16.4 million pandemic-related threats, mostly stemming from spam.
As the pandemic sent employees out of the office, Trend Micro noted a rise in attacks on remote workers' homes. Attacks on devices in homes rose 210% from 929 million in 2019 to nearly 2.9 billion in 2020. Trend Micro saw the number of routers subject to inbound attacks rise from 1.14 million in 2019 to 1.49 million in 2020 and noted that those suffering from outbound attacks, in which malicious actors used routers to launch further attacks, also rose.
Overall, the report estimated that 15.5% of routers connected to Trend Micro's Smart Home Network system suffered inbound attacks.
Brute force attacks topped the inbound attack attempts on home devices, with attempts on NETBIOS SMB usernames reaching 1.4 billion and RDP-based brute-force logins reached 618.5 million in 2020.
RELATED RESOURCE

How to improve cyber security for remote working
13 recommendations for security from any location
The report also saw attackers targeting VPN software, capitalizing on vulnerabilities in Fortinet's VPN and the Pulse Connect Secure VPN. The company detected almost 800,000 probes of the Pulse vulnerability, noting it had been used in attacks delivering the Sodinokibi ransomware.
Trend Micro discovered 127 new ransomware families in 2020, 34% more than it found in 2019. A notable new entrant was the Egregor ransomware, which ranked in the top 10 for detected infections despite its initial detection coming in September 2020.
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Despite Egregor's success, 2017's WannaCry is still the most-detected malware family by far, with 220,166 detections infected. The next most popular was Locky, with just 15,816 cases.
Governments were hardest-hit by ransomware attacks, with 31,906 cases. The second-most affected sector was banking, with 22,082 cases.
Trend Micro also noticed an interesting trend in phishing attacks. The number of non-unique phishing URLs decreased slightly, while the number of unique phishing URLs blocked increased from 161.7 million to 194.5 million. The company stated attackers might be targeting their victims more with custom URLs.
Danny Bradbury has been a print journalist specialising in technology since 1989 and a freelance writer since 1994. He has written for national publications on both sides of the Atlantic and has won awards for his investigative cybersecurity journalism work and his arts and culture writing.
Danny writes about many different technology issues for audiences ranging from consumers through to software developers and CIOs. He also ghostwrites articles for many C-suite business executives in the technology sector and has worked as a presenter for multiple webinars and podcasts.
-
 Why keeping track of AI assistants can be a tricky business
Why keeping track of AI assistants can be a tricky businessColumn Making the most of AI assistants means understanding what they can do – and what the workforce wants from them
By Stephen Pritchard
-
 Nvidia braces for a $5.5 billion hit as tariffs reach the semiconductor industry
Nvidia braces for a $5.5 billion hit as tariffs reach the semiconductor industryNews The chipmaker says its H20 chips need a special license as its share price plummets
By Bobby Hellard
-
 Phishing emails target victims with fake vaccine passport offer
Phishing emails target victims with fake vaccine passport offerNews Scammers could steal victims’ personal information and never deliver the illegal goods, Fortinet warns
By Rene Millman
-
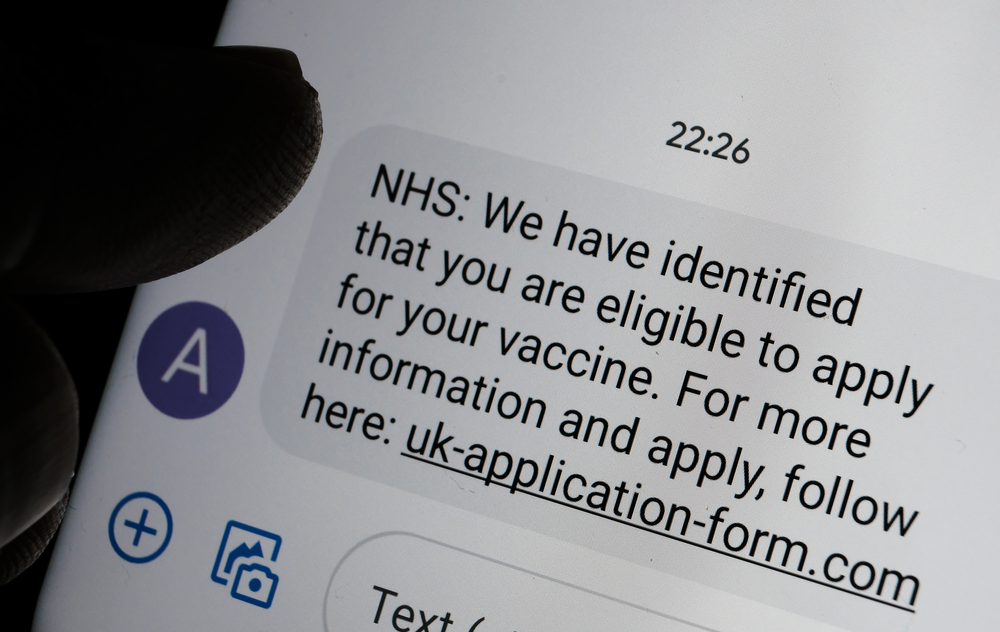 COVID-related phishing fuels a 15-fold increase in NCSC takedowns
COVID-related phishing fuels a 15-fold increase in NCSC takedownsNews The NCSC recorded a significant jump in the number of attacks using NHS branding to lure victims
By Bobby Hellard
-
 COVID vaccine passports will fail unless government wins public trust, ICO warns
COVID vaccine passports will fail unless government wins public trust, ICO warnsNews Data watchdog's chief Elizabeth Denham warns that it’s not good enough to claim ‘this is important, so trust us’
By Keumars Afifi-Sabet
-
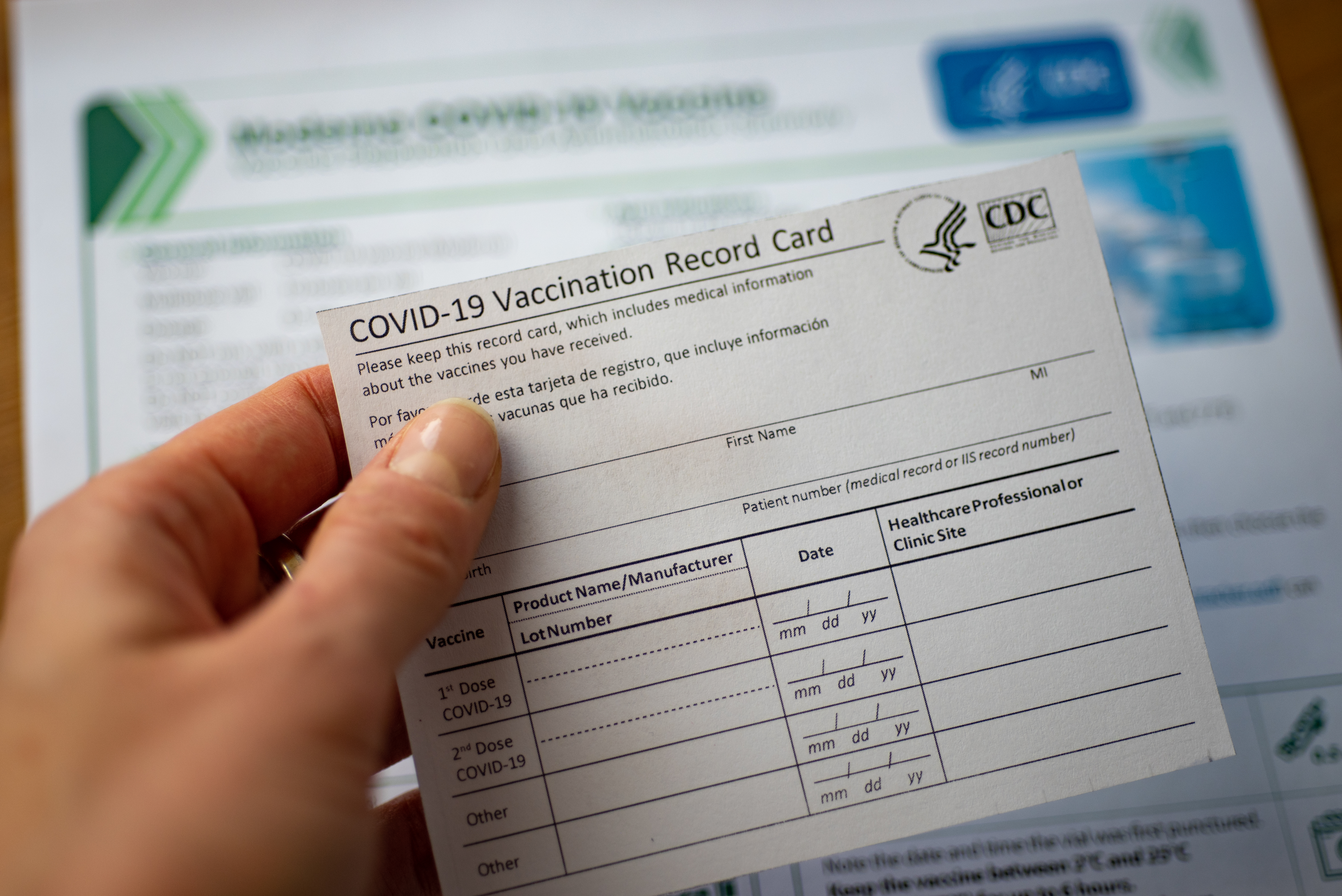 Fake COVID vaccination certificates available on the dark web
Fake COVID vaccination certificates available on the dark webNews Fast-growing market emerges for people wanting quick vaccine proof to travel abroad
By Rene Millman
-
 Hackers using COVID vaccine as a lure to spread malware
Hackers using COVID vaccine as a lure to spread malwareNews Cyber criminals are impersonating WHO, DHL, and vaccine manufacturers in phishing campaigns
By Rene Millman
-
 Website problems slow coronavirus vaccine rollout
Website problems slow coronavirus vaccine rolloutNews Florida is the epicenter of website issues, as patients struggle with malfunctioning sites and hackers
By Danny Bradbury
-
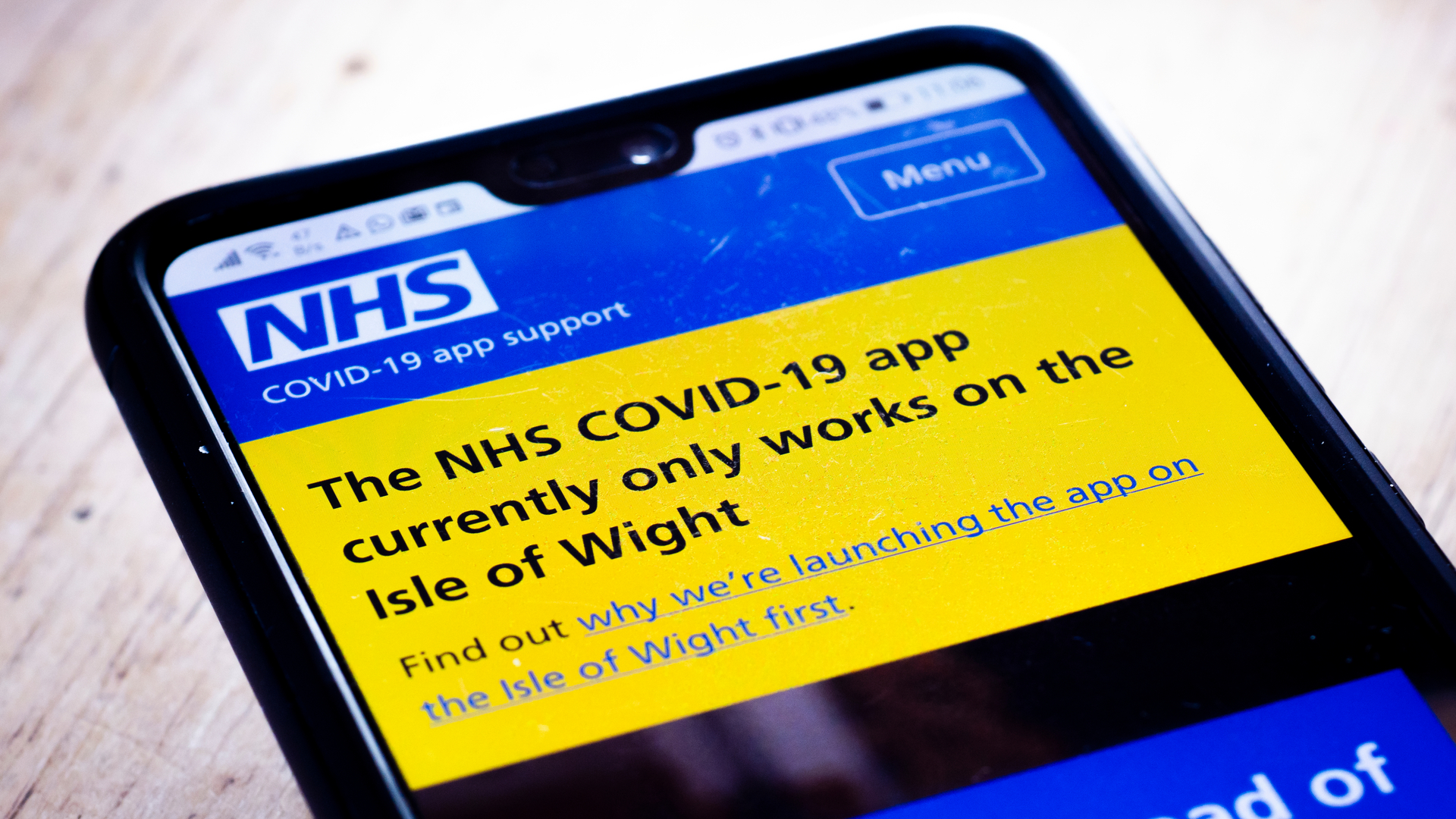 NHS COVID-19 app failed to ask users to self-isolate due to 'software glitch'
NHS COVID-19 app failed to ask users to self-isolate due to 'software glitch'News The bug is the latest in a long line of errors and glitches to plague the government's contact-tracing app
By Keumars Afifi-Sabet
-
 How businesses were left to scramble over data collection for coronavirus contact tracing
How businesses were left to scramble over data collection for coronavirus contact tracingIn-depth The lack of sufficient advice has opened the door for third-party tech firms to normalise massive-scale data harvesting
By Keumars Afifi-Sabet